PCSpoof: New Vulnerability Affects Networking Tech Used By Spacecraft And Aircraft
 |
| Credit: Marina Minkin |
A novel attack method has been disclosed against a crucial piece of technology called time-triggered ethernet (TTE) that's used in safety-critical infrastructure, potentially causing the failure of systems powering spacecraft and aircraft.
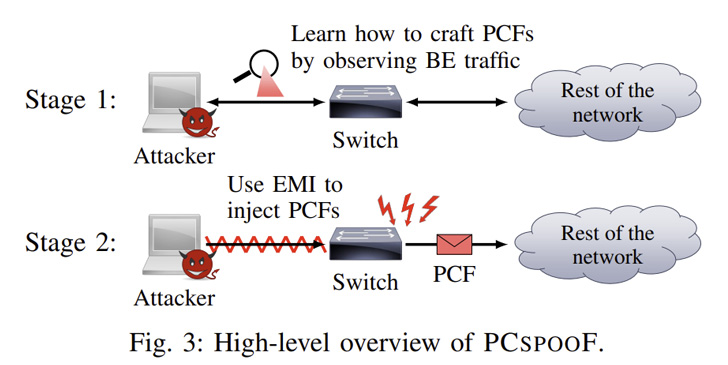
Dubbed PCspooF by a group of academics and researchers from the University of Michigan, the University of Pennsylvania, and the NASA Johnson Space Center, the technique is designed to break TTE's security guarantees and induce TTE devices to lose synchronization for up to a second, a behavior that can even lead to uncontrolled maneuvers in spaceflight missions and threaten crew safety.
TTE is one among the networking technologies that's part of what's called a mixed-criticality network wherein traffic with different timing and faults tolerance requirements coexist in the same physical network. This means that both critical devices, which, say, enable vehicle control, and non-critical devices, which are used for monitoring and data collection, share the same network.
An obvious advantage to this approach is the fact that there are lesser weight and power requirements as well as lower development and time costs stemming as a result of relying on just one technology. But this also comes with drawbacks of its own.
"This mixed-criticality approach puts a lot more pressure on the design of the network to provide isolation," Andrew Loveless, the lead author of the study, told The Hacker News. "Now that critical and non-critical items may connect to the same switch, the network protocol and hardware need to do extra work to make sure the critical traffic is always guaranteed to get through successfully and on time."
 |
| Credit: European Space Agency |
On top of that, while critical devices in the network are subjected to thorough vetting, the non-critical counterparts are not only commercial-off-the-shelf (COTS) devices but also lack the same rigorous process, leading to possible avenues for supply chain compromises that could be weaponized to activate the attack by integrating a rogue third-party component into the system.
This is where a mixed-criticality network helps ensure that even if the COTS device is malicious, it cannot interfere with critical traffic.
"In PCspooF, we uncovered a way for a malicious non-critical device to break this isolation guarantee in a TTE network," Baris Kasikci, an assistant professor in the electrical engineering and computer science department at the University of Michigan, told the publication.
This, in turn, is achieved by using the nefarious device to inject electromagnetic interference (EMI) into a TTE switch over an Ethernet cable, effectively tricking the switch into sending authentic-looking synchronization messages (i.e., protocol control frames or PCFs) and get them accepted by other TTE devices.
Such an "electrical noise" generation circuit can take up as little as 2.5cm × 2.5cm on a single-layer printed circuit board, requiring only minimal power and which can be concealed in a best-effort device and integrated into a TTE system without raising any red flags.
As mitigations, the study recommends using optocouplers or surge protectors to block electromagnetic interference, checking the source MAC addresses to ensure they're authentic, hiding key PCF fields, using a link-layer authentication protocol like IEEE 802.1AE, increasing the number of sync masters, and disabling dangerous state transitions.
The findings show that the use of common hardware in a system engineered to provide strict isolation assurances can sometimes defeat those very protections, the researchers pointed out, adding mixed-criticality software systems should be examined meticulously in a similar manner to ensure the isolation mechanisms are foolproof.
"The TTE protocols are very mature and well-vetted, and many of the most important parts are formally proven," Kasikci said.
"In a way that is what makes our attack interesting – that we were able to figure out how to violate some guarantees of the protocol despite its maturity. But to do that, we had to think outside the box and figure out how to make the hardware behave in a way the protocol does not expect."
Source: thehackernews.com
 Reviewed by Zion3R
on
9:53 AM
Rating:
Reviewed by Zion3R
on
9:53 AM
Rating: