Critical RCE Bug Could Let Hackers Remotely Take Over DrayTek Vigor Routers
As many as 29 different router models from DrayTek have been identified as affected by a new critical, unauthenticated, remote code execution vulnerability that, if successfully exploited, could lead to full compromise of the device and unauthorized access to the broader network.
"The attack can be performed without user interaction if the management interface of the device has been configured to be internet facing," Trellix researcher Philippe Laulheret said. "A one-click attack can also be performed from within the LAN in the default device configuration."
Filed under CVE-2022-32548, the vulnerability has received the maximum severity rating of 10.0 on the CVSS scoring system, owing to its ability to completely allow an adversary to seize control of the routers.
At its core, the shortcoming is the result of a buffer overflow flaw in the web management interface ("/cgi-bin/wlogin.cgi"), which can be weaponized by a malicious actor by supplying specially crafted input.
"The consequence of this attack is a takeover of the so-called 'DrayOS' that implements the router functionalities," Laulheret said. "On devices that have an underlying Linux operating system (such as the Vigor 3910) it is then possible to pivot to the underlying operating system and establish a reliable foothold on the device and local network."
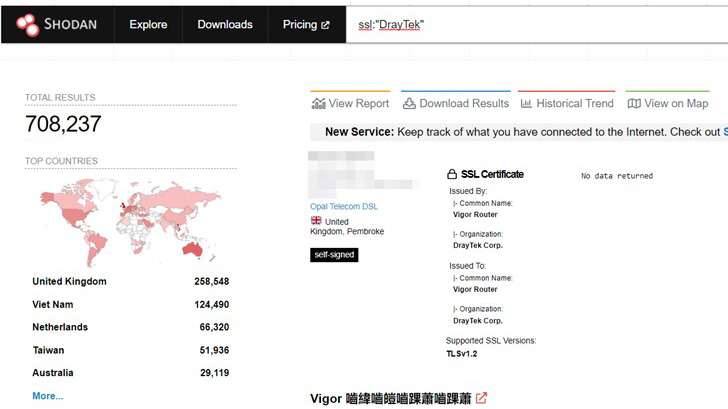
Over 200,000 devices from the Taiwanese manufacturer are said to have the vulnerable service currently exposed on the internet and would require no user interaction to be exploited.
The breach of a network appliance such as Vigor 3910 could not only leave a network open to malicious actions such as credential and intellectual property theft, botnet activity, or a ransomware attack, but also cause a denial-of-service (DoS) condition.
The disclosure comes a little over a month after it emerged that routers from ASUS, Cisco, DrayTek, and NETGEAR are under assault from a new malware called ZuoRAT targeting North American and European networks.
While there are no signs of exploitation of the vulnerability in the wild so far, it's recommended to apply the firmware patches as soon as possible to secure against potential threats.
"Edge devices, such as the Vigor 3910 router, live on the boundary between internal and external networks," Laulheret noted. "As such they are a prime target for cybercriminals and threat actors alike. Remotely breaching edge devices can lead to a full compromise of the businesses' internal network."
Source: thehackernews.com
 Reviewed by Zion3R
on
7:16 AM
Rating:
Reviewed by Zion3R
on
7:16 AM
Rating: