Ukrainian Authorities Arrested Phishing Gang That Stole 100 Million UAH
The Cyber Police of Ukraine last week disclosed that it apprehended nine members of a criminal gang that embezzled 100 million hryvnias via hundreds of phishing sites that claimed to offer financial assistance to Ukrainian citizens as part of a campaign aimed at capitalizing on the ongoing conflict.
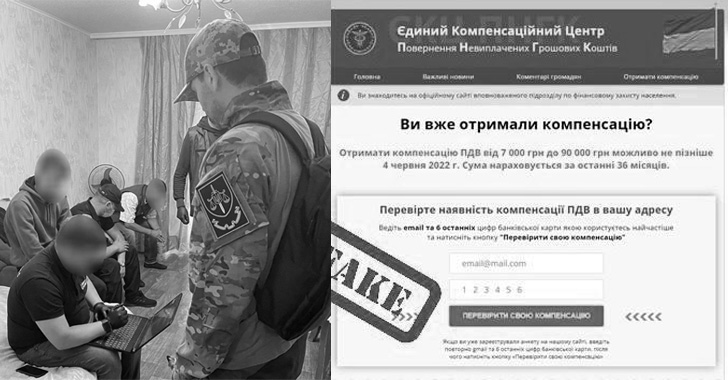
"Criminals created more than 400 phishing links to obtain bank card data of citizens and appropriate money from their accounts," the agency said in a press statement last week. "The perpetrators may face up to 15 years behind bars."
The law enforcement operation culminated in the seizure of computer equipment, mobile phones, bank cards as well as the criminal proceeds illicitly obtained through the scheme.
Some of the rogue domains registered by the actors included ross0.yolasite[.]com, foundationua[.]com, ua-compensation[.]buzz, www.bless12[.]store, help-compensation[.]xyz, newsukraine10.yolasite[.]com, and euro24dopomoga0.yolasite[.]com, among others.
The rogue landing pages, which were designed to siphon people's banking information, operated under the guise of surveys designed to fill up an application for payment of financial assistance from E.U. countries, underscoring the opportunistic nature of the social engineering attack.
Once in possession of the bank details, the threat actors unauthorizedly logged into the accounts and fraudulently withdrew money totaling more than 100 million hryvnias ($3.37 million) from over 5,000 citizens.
The distribution vector used to propagate the links is not immediately clear, but it could have been achieved through different methods such as SMS phishing (aka smishing), spam emails, direct messages on social media apps, SEO poisoning, or seemingly benign ads.
The agency has also warned citizens to "obtain information about financial payments only from official sources, not to click on dubious links, and in no case to communicate confidential, in particular banking, information to third parties or to indicate such data on suspicious resources."
Source: thehackernews.com
 Reviewed by Zion3R
on
6:02 AM
Rating:
Reviewed by Zion3R
on
6:02 AM
Rating: