New Saitama Backdoor Targeted Official From Jordan's Foreign Ministry
A spear-phishing campaign targeting Jordan's foreign ministry has been observed dropping a new stealthy backdoor dubbed Saitama.
Researchers from Malwarebytes and Fortinet FortiGuard Labs attributed the campaign to an Iranian cyber espionage threat actor tracked under the moniker APT34, citing resemblances to past campaigns staged by the group.
"Like many of these attacks, the email contained a malicious attachment," Fortinet researcher Fred Gutierrez said. "However, the attached threat was not a garden-variety malware. Instead, it had the capabilities and techniques usually associated with advanced persistent threats (APTs)."
APT34, also known as OilRig, Helix Kitten, and Cobalt Gypsy, is known to be active since at least 2014 and has a track record of striking telecom, government, defense, oil, and financial sectors in the Middle East and North Africa (MENA) via targeted phishing attacks.
Earlier this February, ESET tied the group to a long-running intelligence gather operation aimed at diplomatic organizations, technology companies, and medical organizations in Israel, Tunisia, and the United Arab Emirates.
The newly observed phishing message contains a weaponized Microsoft Excel document, opening which prompts a potential victim to enable macros, leading to the execution of a malicious Visual Basic Application (VBA) macro that drops the malware payload ("update.exe").
Furthermore, the macro takes care of establishing persistence for the implant by adding a scheduled task that repeats every four hours.
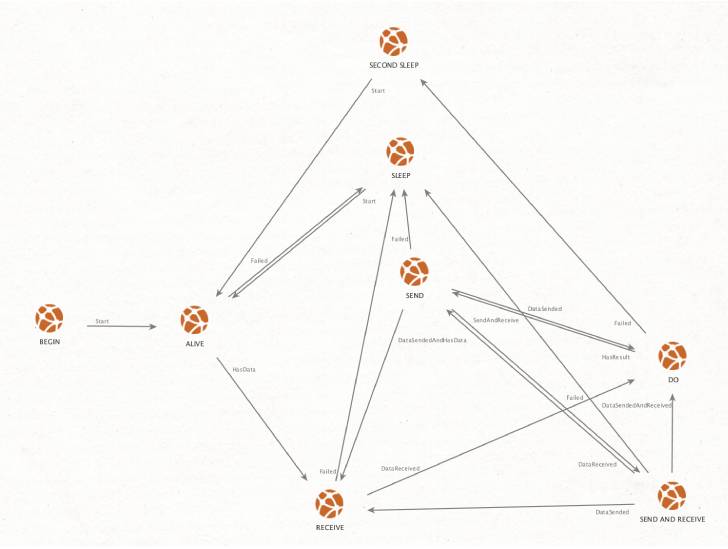
A .NET-based binary, Saitama leverages the DNS protocol for its command-and-control (C2) communications as part of an effort to disguise its traffic, while employing a "finite-state machine" approach to executing commands received from a C2 server.
"In the end, this basically means that this malware is receiving tasks inside a DNS response," Gutierrez explained. DNS tunneling, as it's called, makes it possible to encode the data of other programs or protocols in DNS queries and responses.
In the final stage, the results of the command execution are subsequently sent back to the C2 server, with the exfiltrated data built into a DNS request.
"With the amount of work put into developing this malware, it does not appear to be the type to execute once and then delete itself, like other stealthy infostealers," Gutierrez said.
"Perhaps to avoid triggering any behavioral detections, this malware also does not create any persistence methods. Instead, it relies on the Excel macro to create persistence by way of a scheduled task."
Source: thehackernews.com
 Reviewed by Zion3R
on
6:40 AM
Rating:
Reviewed by Zion3R
on
6:40 AM
Rating: