Malware Attack On South Korean Entities Was Work Of Andariel Group
A malware campaign targeting South Korean entities that came to light earlier this year has been attributed to a North Korean nation-state hacking group called Andariel, once again indicating that Lazarus attackers are following the trends and their arsenal is in constant development.
"The way Windows commands and their options were used in this campaign is almost identical to previous Andariel activity," Russian cybersecurity firm Kaspersky said in a deep-dive published Tuesday. Victims of the attack are in the manufacturing, home network service, media, and construction sectors.
Designated as part of the Lazarus constellation, Andariel is known for unleashing attacks on South Korean organizations and businesses using specifically tailored methods created for maximum effectivity. In September 2019, the sub-group, along with Lazarus and Bluenoroff, was sanctioned by the U.S. Treasury Department for their malicious cyber activity on critical infrastructure.
Andariel is believed to have been active since at least May 2016.
North Korea has been behind an increasingly orchestrated effort aimed at infiltrating computers of financial institutions in South Korea and around the world as well as staging cryptocurrency heists to fund the cash-strapped country in an attempt to circumvent the stranglehold of economic sanctions imposed to stop the development of its nuclear weapons program.
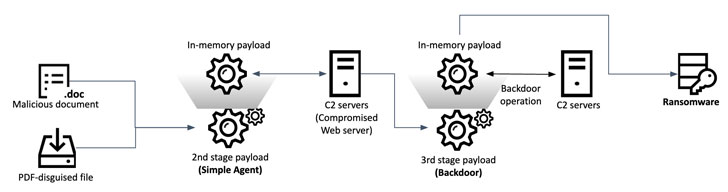
The findings from Kaspersky build upon a previous report from Malwarebytes in April 2021, which documented a novel infection chain that distributed phishing emails weaponized with a macro embedded in a Word file that's executed upon opening in order to deploy malicious code concealed in the form of a bitmap (.BMP) image file to drop a remote access trojan (RAT) on targeted systems.
According to the latest analysis, the threat actor, besides installing a backdoor, is also said to have delivered file-encrypting ransomware to one of its victims, implying a financial motive to the attacks. It's worth noting that Andariel has a track record of attempting to steal bank card information by hacking into ATMs to withdraw cash or sell customer information on the black market.
"This ransomware sample is custom made and specifically developed by the threat actor behind this attack," Kaspersky Senior Security Researcher Seongsu Park said. "This ransomware is controlled by command line parameters and can either retrieve an encryption key from the C2 [server] or, alternatively, as an argument at launch time."
The ransomware is designed to encrypt all files in the machine with the exception of system-critical ".exe," ".dll," ".sys," ".msiins," and ".drv" extensions in return for paying a bitcoin ransom to gain access to a decrypt tool and unique key to unlock the scrambled files.
Kaspersky's attribution to Andariel stems from overlaps in the XOR-based decryption routine that have been incorporated into the group's tactics as early as 2018 and in the post-exploitation commands executed on victim machines.
"The Andariel group has continued to focus on targets in South Korea, but their tools and techniques have evolved considerably," Park said. "The Andariel group intended to spread ransomware through this attack and, by doing so, they have underlined their place as a financially motivated state-sponsored actor."
Source: feedproxy.google.com
 Reviewed by Anonymous
on
5:31 AM
Rating:
Reviewed by Anonymous
on
5:31 AM
Rating: