Bomb Threat Hoaxer Exposed by Hacked Gaming Site
Federal authorities this week arrested a North Carolina man who allegedly ran with a group of online hooligans that attacked Web sites (including this one), took requests on Twitter to call in bomb threats to thousands of schools, and tried to frame various online gaming sites as the culprits. In an ironic twist, the accused — who had fairly well separated his real life identity from his online personas — appears to have been caught after a gaming Web site he frequented got hacked.
On Feb. 12, the U.S. Justice Department announced the arrest of Timothy Dalton Vaughn, a 20-year-old from Winston-Salem, N.C. Vaughn is alleged to have been a key member of the Apophis Squad, a gang of ne’er-do-wells who made bomb threats against thousands of schools and launched distributed denial-of-service (DDoS) attacks against Web sites — including KrebsOnSecurity on multiple occasions.
The feds say Vaughn used multiple aliases on Twitter and elsewhere to crow about his attacks, including “HDGZero,” “WantedByFeds,” and “Xavier Farbel.” Among the Apophis Squad’s targets was encrypted mail service Protonmail, which reached out to this author last year for clues about the identities of the Apophis Squad members after noticing we were both being targeted by them and receiving demands for money in exchange for calling off the attacks.
Protonmail later publicly thanked KrebsOnSecurity for helping to bring about the arrest of Apophis Squad leader George Duke-Cohan — a.k.a. “opt1cz,” “7R1D3n7,” and “Pl3xl3t,” — a 19-year-old from the United Kingdom who was convicted in December 2018 and sentenced to three years in prison. But the real-life identity of HDGZero remained a mystery to both of us, as there was little publicly available information at the time connecting that moniker to anyone.
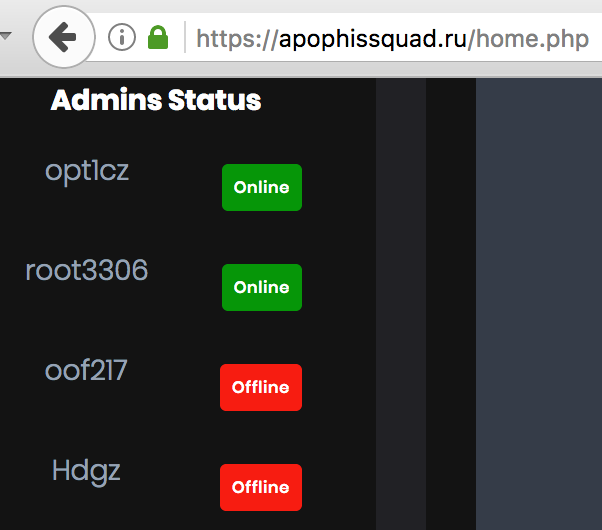
The DDoS-for-hire service run by Apophis Squad listed their members.
That is, until early January 2019, when news broke that hackers had broken into the servers of computer game maker BlankMediaGames and made off with account details of some 7.6 million people who had signed up to play “Town of Salem, the company’s browser-based role playing game. That stolen information has since been posted and resold in underground forums.
A review of the leaked BlankMediaGames user database shows that in late 2018, someone who selected the username “hdgzero” signed up to play Town of Salem, registering with the email address xavierfarbel@gmail.com. The data also shows this person registered at the site using a Sprint mobile device with an Internet address that traced back to the Carolinas.
The Justice Department indictment against Vaughn and Duke-Cohan released this week alleges the pair were equally responsible for sending spoofed bomb threat emails to 2,000 schools in the United States and more than 400 in the U.K., falsely warning that various explosive devices were planted at the schools and would be detonated unless a ransom demand was paid.
In this snippet from a January 2018 online chat taken from a channel maintained by HDGZero, the accused can be seen claiming credit for the bomb threats and posting links to stories in various local media outlets about schools evacuating students in response to the threats. The bomb threat emails were made to look like they were sent by different high-profile squads of online gamers competing against one another in the wildly popular game Minecraft.
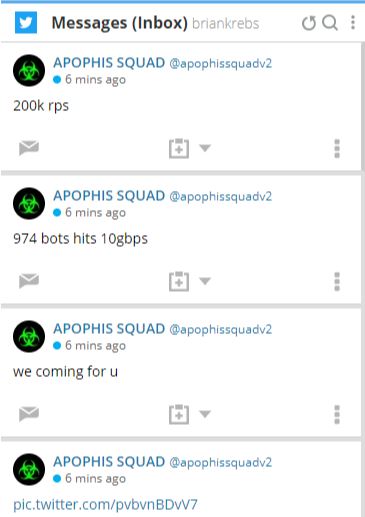
One of the many private Twitter messages I received from the Apophis Squad following DDoS attacks on KrebsOnSecurity.
The government maintains that, through their various Twitter handles, Duke-Cohan and Vaughn even offered to take requests for shutting down specific schools with bomb threats.
“We are OPEN for request for school lockdowns / evacs,” read a tweet from the Twitter account @apophissquadv2, which the Justice Department says Duke-Cohan and Vaughn shared. “Send us your request to apophissquad@tuta.io (FREE).”
The government alleges that Vaughn also participated with Duke-Cohan in reporting the hijack of a United Airlines flight bound for the United States. That flight, which had almost 300 passengers on board, was later quarantined for four hours in San Francisco pending a full security check.
The indictment charges Vaughn and Duke-Cohan with conspiracy and eight additional felony offenses, including making threats to injure in interstate commerce and making interstate threats involving explosives. Vaughn is additionally charged with intentionally damaging a computer and interstate threat to damage a protected computer with intent to extort.
A Justice Department press release on the indictment states that if convicted of all 11 charges, Vaughn would face a statutory maximum sentence of 80 years in federal prison. If convicted of the nine charges in the indictment in which he is named, Duke-Cohan would face a statutory maximum sentence of 65 years in federal prison.
Source: krebsonsecurity.com
 Reviewed by Anonymous
on
9:56 PM
Rating:
Reviewed by Anonymous
on
9:56 PM
Rating:





