GovPayNow.com Leaks 14M+ Records
Government Payment Service Inc. — a company used by thousands of U.S. state and local governments to accept online payments for everything from traffic citations and licensing fees to bail payments and court-ordered fines — has leaked more than 14 million customer records dating back at least six years, including names, addresses, phone numbers and the last four digits of the payer’s credit card.
Indianapolis-based GovPayNet, doing business online as GovPayNow.com, serves approximately 2,300 government agencies in 35 states. GovPayNow.com displays an online receipt when citizens use it to settle state and local government fees and fines via the site. Until this past weekend it was possible to view millions of customer records simply by altering digits in the Web address displayed by each receipt.
On Friday, Sept. 14, KrebsOnSecurity alerted GovPayNet that its site was exposing at least 14 million customer receipts dating back to 2012. Two days later, the company said it had addressed “a potential issue.”
“GovPayNet has addressed a potential issue with our online system that allows users to access copies of their receipts, but did not adequately restrict access only to authorized recipients,” the company said in a statement provided to KrebsOnSecurity.
The statement continues:
“The company has no indication that any improperly accessed information was used to harm any customer, and receipts do not contain information that can be used to initiate a financial transaction. Additionally, most information in the receipts is a matter of public record that may be accessed through other means. Nonetheless, out of an abundance of caution and to maximize security for users, GovPayNet has updated this system to ensure that only authorized users will be able to view their individual receipts. We will continue to evaluate security and access to all systems and customer records.”
In January 2018, GovPayNet was acquired by Securus Technologies, a Carrollton, Texas- based company that provides telecommunications services to prisons and helps law enforcement personnel keep tabs on mobile devices used by former inmates.
Although its name may suggest otherwise, Securus does not have a great track record in securing data. In May 2018, the New York Times broke the news that Securus’ service for tracking the cell phones of convicted felons was being abused by law enforcement agencies to track the real-time location of mobile devices used by people who had only been suspected of committing a crime. The story observed that authorities could use the service to track the real-time location of nearly any mobile phone in North America.
Just weeks later, Motherboard reported that hackers had broken into Securus’ systems and stolen the online credentials for multiple law enforcement officials who used the company’s systems to track the location of suspects via their mobile phone number.
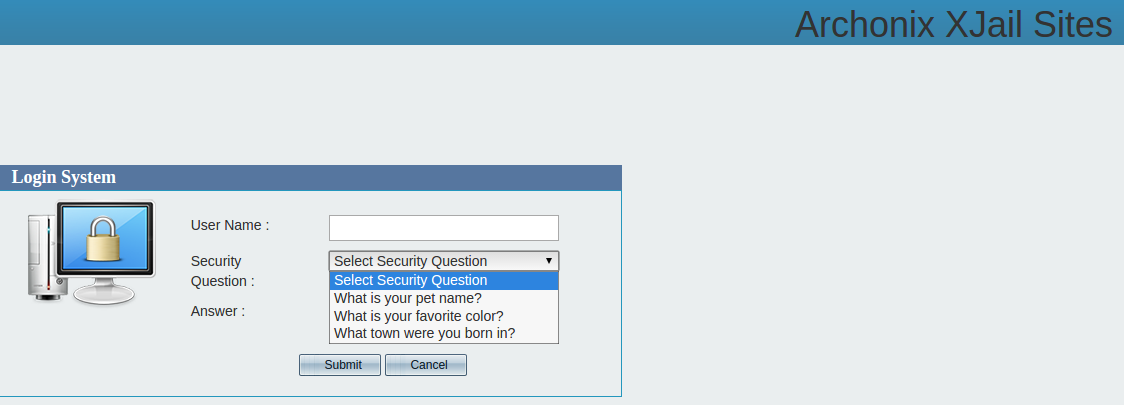
A story here on May 22 illustrated how Securus’ site appeared to allow anyone to reset the password of an authorized Securus user simply by guessing the answer to one of three pre-selected “security questions,” including “what is your pet name,” “what is your favorite color,” and “what town were you born in”. Much like GovPayNet, the Securus Web site seemed to have been erected sometime in the aughts and left to age ungracefully for years.
Data exposures like these are some of the most common but easily preventable forms of information leaks online. In every case, it was trivial to enumerate how many records were exposed because each record was sequential.
E-commerce sites can mitigate such leaks by using something other than easily-guessed or sequential record numbers, and/or encrypting unique portions of the URL displayed to customers upon payment.
Although fixing these information disclosure vulnerabilities is quite simple, it’s remarkable how many organizations that should know better don’t invest the resources needed to find and fix them. In August, KrebsOnSecurity disclosed a similar flaw at work across hundreds of small bank Web sites run by Fiserv, a major provider of technology services to financial institutions.
In July, identity theft protection service LifeLock fixed an information disclosure flaw that needlessly exposed the email address of millions of subscribers. And in April 2018, PaneraBread.com remedied a weakness that exposed millions of customer names, email and physical addresses, birthdays and partial credit card numbers.
Got a tip about a security vulnerability similar to those detailed above, or perhaps something more serious? Please drop me a note at krebsonsecurity @ gmail.com.
Source: krebsonsecurity.com
 Reviewed by Anonymous
on
3:09 PM
Rating:
Reviewed by Anonymous
on
3:09 PM
Rating: