Reverse Engineering Toolset And Fuzzing Protobuf-based Apps
Reverse Engineering Toolset And Fuzzing Protobuf-based Apps
Protobuf is a serialization format developed by Google and used in an increasing number of Android, web, desktop and more applications. It consists of a language for declaring data structures, which is then compiled to code or another kind of structure depending on the target implementation.
pbtk (Protobuf toolkit) is a full-fledged set of scripts, accessible through an unified GUI, that provides two main features:
- Extracting Protobuf structures from programs, converting them back into readable .protos, supporting various implementations:
All the main Java runtimes (base, Lite, Nano, Micro, J2ME), with full Proguard support,
Binaries containing embedded reflection metadata (typically C++, sometimes Java and most other bindings),
Web applications using the JsProtoUrl runtime.
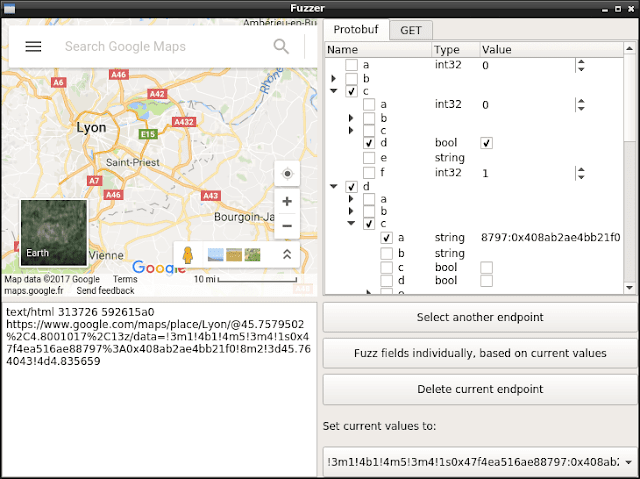
- Editing, replaying and fuzzing data sent to Protobuf network endpoints, through a handy graphical interface that allows you to edit live the fields for a Protobuf message and view the result.
Installation
PBTK requires Python ≥ 3.6, PyQt 5, Python-Protobuf 3, and a handful of executable programs (chromium, jad, dex2jar...) for running extractor scripts.
Archlinux users can install directly through the package:
$ yaourt -S pbtk-git
$ pbtk
On most distributions, you'll want to run the cx_freeze executable (bundling Python 3.6 along with all modules):
$ wget https://github.com/marin-m/pbtk/releases/download/1.0.1/pbtk-1.0.1-linux-cxfreeze.tar.gz
$ tar xvf pbtk-1.0.1-linux-cxfreeze.tar.gz && cd pbtk-1.0.1-linux-cxfreeze
$ ./gui
Or run it directly if you have the required dependencies:
$ git clone https://github.com/marin-m/pbtk
$ cd pbtk
$ ./gui.py
Windows support is untested yet. Once you run the GUI, it should warn you on what you are missing depending on what you try to do.
Command line usage
The GUI can be lanched through the main script:./gui.py
The following scripts can also be used standalone, without a GUI:
./extractors/jar_extract.py [-h] input_file [output_dir]
./extractors/from_binary.py [-h] input_file [output_dir]
./extractors/web_extract.py [-h] input_url [output_dir]
Scripts don't have an extension and are at root of archive when you use the cx_freeze image.
Download
Source: blog.hackersonlineclub.com
Reverse Engineering Toolset And Fuzzing Protobuf-based Apps
 Reviewed by Anonymous
on
6:11 AM
Rating:
Reviewed by Anonymous
on
6:11 AM
Rating:
 Reviewed by Anonymous
on
6:11 AM
Rating:
Reviewed by Anonymous
on
6:11 AM
Rating: