Web Trackers Caught Intercepting Online Forms Even Before Users Hit Submit
A new research published by academics from KU Leuven, Radboud University, and the University of Lausanne has revealed that users' email addresses are exfiltrated to tracking, marketing, and analytics domains before such is submitted and without prior consent.
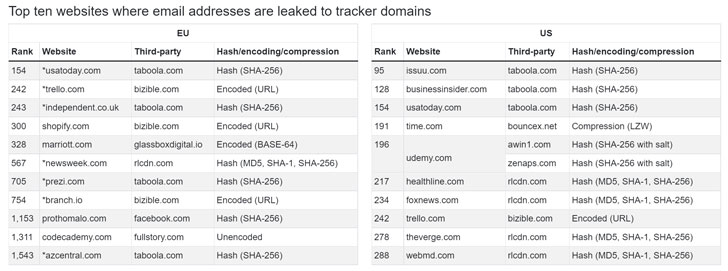
The study involved crawling 2.8 million pages from the top 100 websites, and found that as many as 1,844 websites allowed trackers to capture email addresses before form submission in the European Union, a number that jumped to 2,950 when the same set of websites are visited from the U.S.
"Emails (or their hashes) were sent to 174 distinct domains (eTLD+1) in the U.S. crawl, and 157 distinct domains in the EU crawl," the researchers said. Furthermore, 52 websites were determined to be collecting passwords in the same manner, an issue that has since been addressed following responsible disclosure.
LiveRamp, Taboola, Adobe, Verizon, Yandex, Meta, TikTok, Salesforce, Listrak, and Oracle are some of the top third-party trackers that have been spotted logging email addresses, while Yandex, Mixpanel, and LogRocket lead the list in the password-grabbing category.
Email addresses pose a number of advantages. Not only are they unique, enabling third-parties to track users across devices, it can also be employed to match their online and offline activities, say, in scenarios where they make an in-store purchase that requires them to share their email address or sign up for a loyalty card.
The idea behind harvesting email addresses entered in online forms, even in cases where the users do not submit any form, has also been fueled by ongoing attempts by browser vendors to drop support for third-party cookies, forcing marketers to look for alternative static identifiers to track users.
This is not the first time such a concern has been raised. In June 2017, Gizmodo discovered that a third party called NaviStone was collecting personal information from mortgage calculator forms prior to their submission, with very few websites explicitly disclosing this practice in their privacy policy.
Fast forward five years later, not much has changed, the researchers said, what with websites related to fashion/beauty, online shopping, and general news emerging as the top categories with the most "leaky forms."
"Despite filling email fields on hundreds of websites categorized as pornography, we have not a single email leak," the findings show, noting how it lines up with previous studies that have shown that adult websites have relatively fewer third-party trackers when compared to general sites with comparable popularity.
What's more, such a practice may be in violation of at least three different General Data Protection Regulation (GDPR) requirements in the E.U., contravening principles of transparency, purpose limitation, and user consent.
"Users should assume that the personal information they enter into web forms may be collected by trackers—even if the form is never submitted," the researchers concluded, calling on a further investigation from browser vendors, privacy tool developers, and data protection agencies.
Source: thehackernews.com
 Reviewed by Zion3R
on
11:40 PM
Rating:
Reviewed by Zion3R
on
11:40 PM
Rating: