NVIDIA Jetson Chipsets Found Vulnerable To High-severity Flaws
U.S. graphics chip specialist NVIDIA has released software updates to address a total of 26 vulnerabilities impacting its Jetson system-on-module (SOM) series that could be abused by adversaries to escalate privileges and even lead to denial-of-service and information disclosure.
Tracked from CVE‑2021‑34372 through CVE‑2021‑34397, the flaws affect products Jetson TX1, TX2 series, TX2 NX, AGX Xavier series, Xavier NX, and Nano and Nano 2GB running all Jetson Linux versions prior to 32.5.1. The company credited Frédéric Perriot of Apple Media Products for reporting all the issues.
The NVIDIA Jetson line consists of embedded Linux AI and computer vision compute modules and developer kits that primarily caters to AI-based computer vision applications and autonomous systems such as mobile robots and drones.
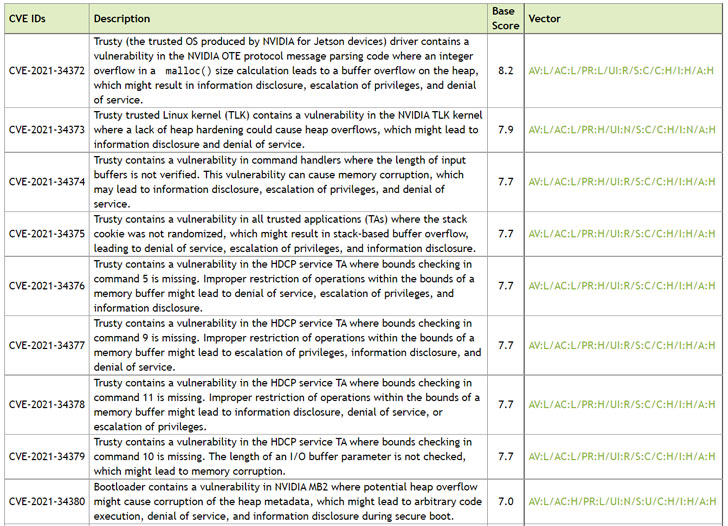
Chief among the vulnerabilities is CVE‑2021‑34372 (CVSS score: 8.2), a buffer overflow flaw in its Trusty trusted execution environment (TEE) that could result in information disclosure, escalation of privileges, and denial-of-service.
Eight other critical weaknesses involve memory corruption, stack overflows, and missing bounds checks in the TEE as well as heap overflows affecting the Bootloader that could lead to arbitrary code execution, denial-of-service, and information disclosure. The rest of the flaws, also related to Trusty and Bootloader, could be exploited to impact code execution, causing denial-of-service and information disclosure, the company noted.
"Earlier software branch releases that support this product are also affected," NVIDIA said. "If you are using an earlier branch release, upgrade to the latest 32.5.1 release. If you are using the 32.5.1 release, update to the latest Debian packages."
Source: feedproxy.google.com
 Reviewed by Anonymous
on
12:25 AM
Rating:
Reviewed by Anonymous
on
12:25 AM
Rating: