Understanding and Configure Snort Rules
Hello friends! Today we are going to explore “How to write any rules in Snort” that could be work as NIDS and NIPS but for this first you need to configure Snort in your machine which we had already discussed in our previous article “IDS, IPS Penetration Testing Lab Setup with Snort”
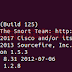
Since I have already configure snort in ubuntu machine therefore now I can proceed for loading rules inside it which will turn enable the NIDS mode of snort. From given image you can read I had installed snort 2.9.11 in my system.
Type snort –V command in terminal to know install version of snort as shown in given below image.

Check your network interface configuration by executing ifconfig command; from here I came to know 192.168.1.103 is my network IP.

Open snort.conf file in text editor by using following command
sudo gedit /etc/snort/snort.conf
Now enter your local network address as HOME_NET as given below in image, here you can also add only your system IP.

Snort Rule Format
Snort offer its user to write their own rule for generating logs of Incoming/Outgoing network packets. Only they need to follow snort rule format where packets must meet the threshold conditions. Always bear in mind that the snort rule can be written by combining two main parts “the Header” and “the Options” segment.
The header part contains information such as the action, protocol, the source IP and port, the network packet Direction operator towards the destination IP and port, the remaining will be consider in the options part.
Syntax: Action Protocol Source IP Source port -> Destination IP Destination port (options)

Header Fields:-
Action: It informs Snort what kind of action to be performed when it discover a packet that matches the rule description. There are five existing default job actions in Snort: alert, log, pass, activate, and dynamic are keyword use to define action of rules. You can also go with additional options which include drop, reject, and sdrop.
Protocol: After deciding the option for action in rule, you need to describe specific Protocol (ip, tcp, udp, icmp, any) on which this rule will be applicable.
Source IP: This part of header describes the sender network interface from which traffic is coming.
Source Port: This part of header describes the source Port from which traffic is coming.
Direction operator (“->”, “<>”): It denotes the direction of traffic flow between sender and receiver networks.
Destination IP: This part of header describes the destination network interface in which traffic is coming for establishing connection.
Destination Port: This part of header describes the destination Port on which traffic is coming for establishing connection.
Option Fields:
The body for rule option is usually written between circular brackets “()” that contains keywords with their argument and separated by semicolon “;” from another keywords.
There are four major categories of rule options.
General: These options contains metadata that offers information with reference to the.
Payload: These options all come across for data contained by the packet payload and can be interconnected.
Non-payload: These options come across for non-payload data.
Post-detection: These options are rule specific triggers that happen after a rule has “fired.”
General Rule Options (Metadata)
In this article are going to explore more about general rule option for beginners so that they can easily write basic rule in snort rule file and able to analyst packet of their network. Metadata is part of optional rule which basically contains addition information of about snort rule that is written with the help of some keywords and with their argument details.
| Keyword | Description |
| msg | The msg keyword stands for “Message” that informs to snort that written argument should be print in logs while analyst of any packet. |
| reference | The reference keyword allows rules to a reference to information present on other systems available on the Internet such as CVE. |
| gid | The gid keyword stands for “Generator ID “which is used to identify which part of Snort create the event when a specific rule will be lunched. |
| sid | The sid keyword stands for “Snort ID” is used to uniquely identify Snort rules. |
| rev | The rev keyword stands for “Revision” is used to uniquely identify revisions of Snort rules. |
| classtype | The classtype keyword is used to assigned classifications and priority numbers to group and distinguish them a rule as detecting an attack that is part of a more general type of attack class. |
Source: www.hackingarticles.in
 Reviewed by Anonymous
on
11:43 PM
Rating:
Reviewed by Anonymous
on
11:43 PM
Rating:





