Gas Pump Skimmer Sends Card Data Via Text
Skimming devices that crooks install inside fuel station gas pumps frequently rely on an embedded Bluetooth component allowing thieves to collect stolen credit card data from the pumps wirelessly with any mobile device. The downside of this approach is that Bluetooth-based skimmers can be detected by anyone else with a mobile device. Now, investigators in the New York say they are starting to see pump skimmers that use cannibalized cell phone components to send stolen card data via text message.
Skimmers that transmit stolen card data wirelessly via GSM text messages and other mobile-based communications methods are not new; they have been present — if not prevalent — in ATM skimming devices for ages.
But this is the first instance KrebsOnSecurity is aware of in which such SMS skimmers have been found inside gas pumps, and that matches the experience of several states hardest hit by pump skimming activity.
The beauty of the GSM-based skimmer is that it can transmit stolen card data wirelessly via text message, meaning thieves can receive real-time transmissions of the card data anywhere in the world — never needing to return to the scene of the crime. That data can then be turned into counterfeit physical copies of the cards.
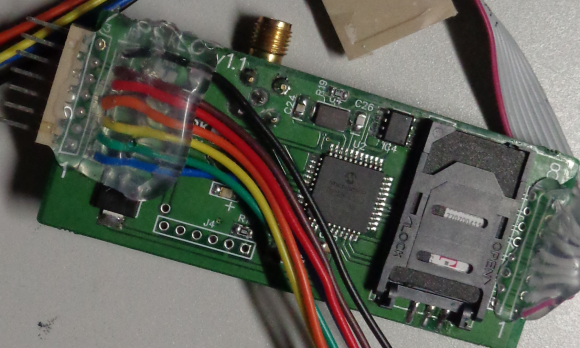
Here’s a look at a new skimmer pulled from compromised gas pumps at three different filling stations in New York this month. Like other pump skimmers, this device was hooked up to the pump’s internal power, allowing it to operate indefinitely without relying on batteries.

A GSM-based card skimmer found embedded in a gas pump in the northeastern United States.
It may be difficult to see from the picture above, but the skimmer includes a GSM-based device with a SIM card produced by cellular operator T-Mobile. The image below shows the other side of the pump skimmer, with the SIM card visible in the upper right corner of the circuitboard:
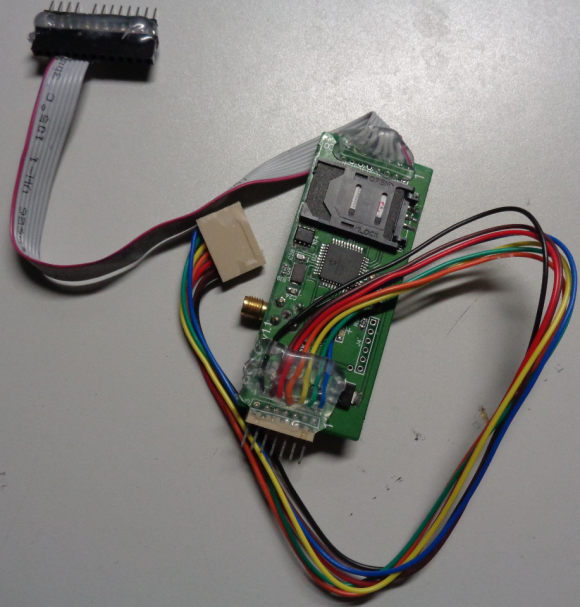
The reverse side of this GSM-based pump skimmer shows a SIM card from T-Mobile.
It’s not clear what type of mobile device was used in this skimmer, and the police officer who shared these images with KrebsOnSecurity said the forensic analysis of the device was ongoing.
Here’s a close-up of the area around the SIM card:
The officer, who shared these photos on condition of anonymity, said this was thought to be the first time fraud investigators in New York had ever encountered a GSM-based pump skimmer.
Skimmers used at all three New York filling stations impacted by the scheme included T-Mobile SIM cards, but the investigator said analysis so far showed the cards held no other data other than the SIM’s card’s unique serial number (ICCID).
KrebsOnSecurity reached out to weights and measures officials in several states most heavily hit by pump skimming activity, including Arizona, California and Florida.
Officials in all three states said they’ve yet to find a GSM-based skimmer attached to any of their pumps.
Skimmers at the pump are most often the work of organized crime rings that traffic in everything from stolen credit and debit cards to the wholesale theft and commercial resale of fuel — in some cases from (and back to) the very fuel stations that have been compromised with the gang’s skimming devices.
Investigators say skimming gangs typically gain access to station pumps by using a handful of master keys that still open a great many pumps in use today. In a common scenario, one person will distract the station attendant as fuel thieves pull up alongside the pump in a van with doors that obscure the machine on both sides. For an in-depth look at the work on one fuel-theft gang working out of San Diego, check out this piece.
There are generally no outward signs when a pump has been compromised by a skimmer, but a study KrebsOnSecurity published last year about a surge in pump skimming activity in Arizona suggests that skimmer gangs can spot the signs of a good mark.
Fraud patterns show fuel theft gangs tend to target stations that are close to major highway arteries; those with older pumps; and those without security cameras, and/or a regular schedule for inspecting security tape placed on the pumps.
Many filling stations are upgrading their pumps to include more physical security — such as custom locks and security cameras. In addition, newer pumps can accommodate more secure chip-based payment cards that are already in use by all other G20 nations.
But these upgrades are disruptive and expensive, and some stations are taking advantage of recent moves by Visa to delay adding much-needed security improvements, such as chip-capable readers.
Until late 2016, fuel station owners in the United States had until October 1, 2017 to install chip-capable readers at their pumps. Under previous Visa rules, station owners that didn’t have chip-ready readers in place by then would have been on the hook to absorb 100 percent of the costs of fraud associated with transactions in which the customer presented a chip-based card yet was not asked or able to dip the chip (currently, card-issuing banks and consumers eat most of the fraud costs from fuel skimming).
But in December 2016, Visa delayed the requirements, saying fuel station owners would now have until October 1, 2020 to meet the liability shift deadline.
The best advice one can give to avoid pump skimmers is to frequent stations that appear to place an emphasis on physical security. More importantly, some pump skimming devices are capable of stealing debit card PINs as well, so it’s good idea to avoid paying with a debit card at the pump.
Armed with your PIN and debit card data, thieves can clone the card and pull money out of your account at an ATM. Having your checking account emptied of cash while your bank sorts out the situation can be a huge hassle and create secondary problems (bounced checks, for instance).
Source: krebsonsecurity.com
 Reviewed by Anonymous
on
4:16 AM
Rating:
Reviewed by Anonymous
on
4:16 AM
Rating: